What can organisations do to improve cyber security?
Make cyber security a business priority
Business leaders and board members must make cyber security a business priority. It shouldn’t simply be an IT decision. Board members and senior managers should take an interest and be updated regularly with the ongoing progress and developments around their organisation’s security activities.
Many security professionals will testify that it is much easier to change the organisational culture to one which embraces good security practices—if the policies and processes are endorsed and enforced by those at the top.
Take a holistic approach to cyber security
Many businesses and charities will frame cybersecurity in different ways. While one company may focus solely on GDPR compliance and protecting personal data, another may focus on preventing hackers from hiding in the network and running stealth operations such as crypto-mining activities. Cyber security appears to mean different things to different people.
What companies should aim to do is to implement a holistic approach to security. That means companies should consider its people, processes and technology and take a wider range of actions around cyber security.
As well as the right technology, many organisations still don’t have cyber security policies, processes and training in place—which are all important in the journey towards a more mature and holistic security posture.
Organisations should also consider the supply-chain risk and potentially assess the security measures and policies that their suppliers have in place—something which is commonly underestimated as a potential source of threats.
Raise staff awareness and training
The survey found that only 27% of businesses and 29% of charities sent staff on training. Considering human error is typically the weakest link, and that many organisations feel they lack skills within cyber security, investing in some training may help increase resilience.
Educating employees on the importance of cyber security measures and increasing employee buy-in for security projects and policies is also an area where training can help. Board members, senior managers and employees need to understand the business risks around cyber security and should understand the indirect costs to breaches such as loss of productivity and reputational damage—not just the obvious costs such as stolen funds.
Be proactive
Another finding from the survey was that many businesses expected information and guidance to be pushed out to them. However, the fact of the matter is that organisations need to be seeking information themselves.
A good starting point for making sure you have the basics covered is the National Cyber Security Centre website and the Government’s Cyber Essentials and Cyber Aware schemes. Plenty of guidance and support is included and once you have implemented the procedures you can gain Cyber Essentials Certification — which demonstrates to your customers and suppliers that you are acting to tackle cyber threats.
You can always continue to invest in, and improve, your security posture once the basics are in place.
Invest in technology
There are a host of security products and solutions available on the market and it can be difficult for organisations to choose which is right for them.
For those companies that are already using Microsoft products such as Windows and Office 365, we would highly recommend looking at Microsoft’s cutting-edge and cloud-based threat protection suite — part of Microsoft 365.
We don’t believe that there is any other security offering on the market with such a compelling offering as Microsoft; the value that companies of all sizes can get from Microsoft 365’s enterprise-grade security offering is exceptional.
If you aren’t sure on how best to utilise the available technologies, speak to a cyber security partner about the possibility of a consultancy project.
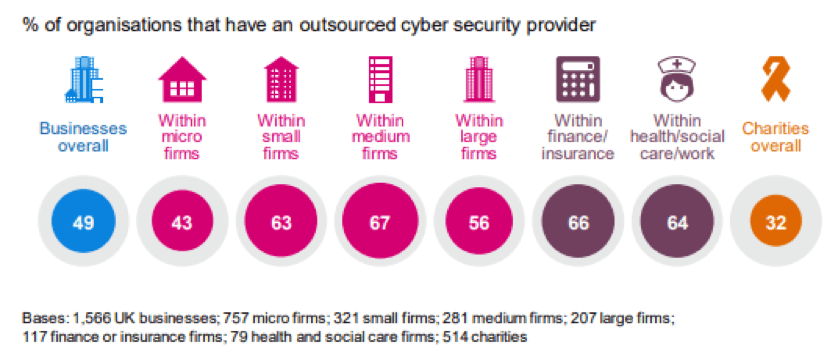
Consider outsourcing to a cyber security partner
It is predicted that there will be a shortage of 3.5 million security staff by 2021—another reason why so many organisations are now opting for managed security service providers (MSSPs) and outsourced Security Operations Centre (SOC) services.
Outsourcing to a cyber security partner can be a cost-effective way of gaining access to a vast array of expertise and experience, whilst also allowing you to offload a significant amount of workload from your internal IT team.
Many organisations that keep security in-house, invest in advanced threat detection software only to find that they don’t know what to do with the threats that they are being alerted to. This is where outsourcing to a SOC might be the best option for organisations that want to increase their cyber resilience.
A Security Operations Centre (SOC) is a dedicated team of cyber security experts that are focused on preventing and responding to cyber-attacks and security breaches. SOCs act as a centralised security hub—receiving telemetry from across IT infrastructure, networks, data and endpoints to gain visibility of the activities and events taking place across these environments. They oversee monitoring to detect potential threats, providing advice on preventative and remedial actions to be taken in response to the threat analytics and assessments that the SOC team generate. This is available as a service where you pay a monthly retainer per device or user.
Again, this gives you access to on-demand expertise, allowing your team to carry on doing their day to day work and giving you piece of mind that your security is in hand.