We all know a strong Conditional Access design is one of the most important security measures to implement to protect your users and data.
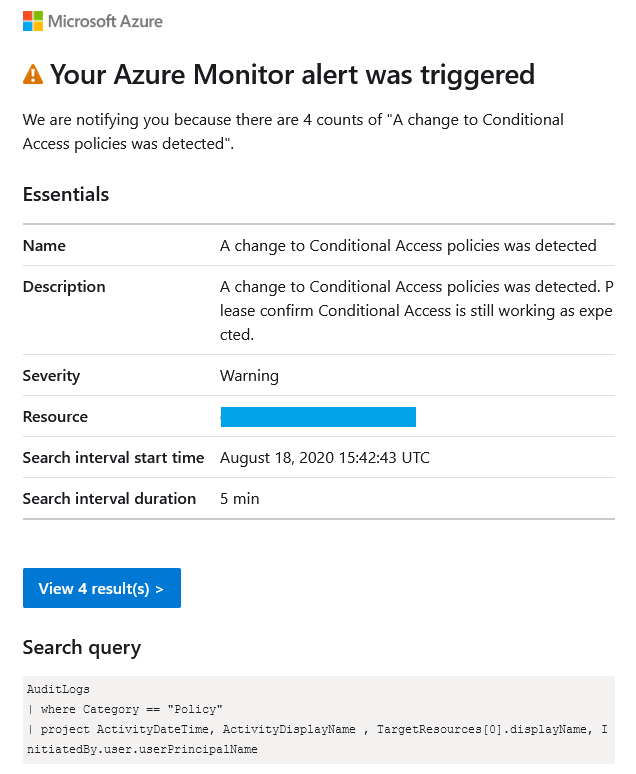
One feature that is currently lacking in Conditional Access is change tracking and alerting. If an admin makes a mistake or a global admin account is breached and Conditional Access is changed, how will you know?
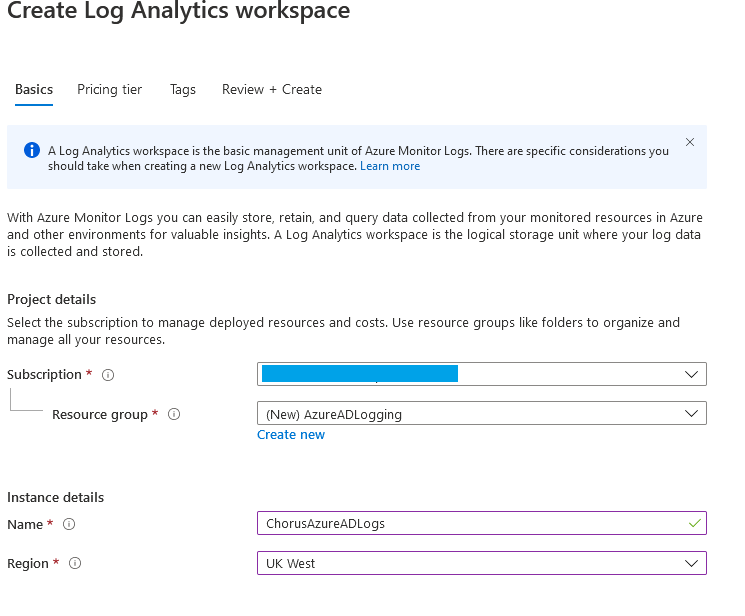
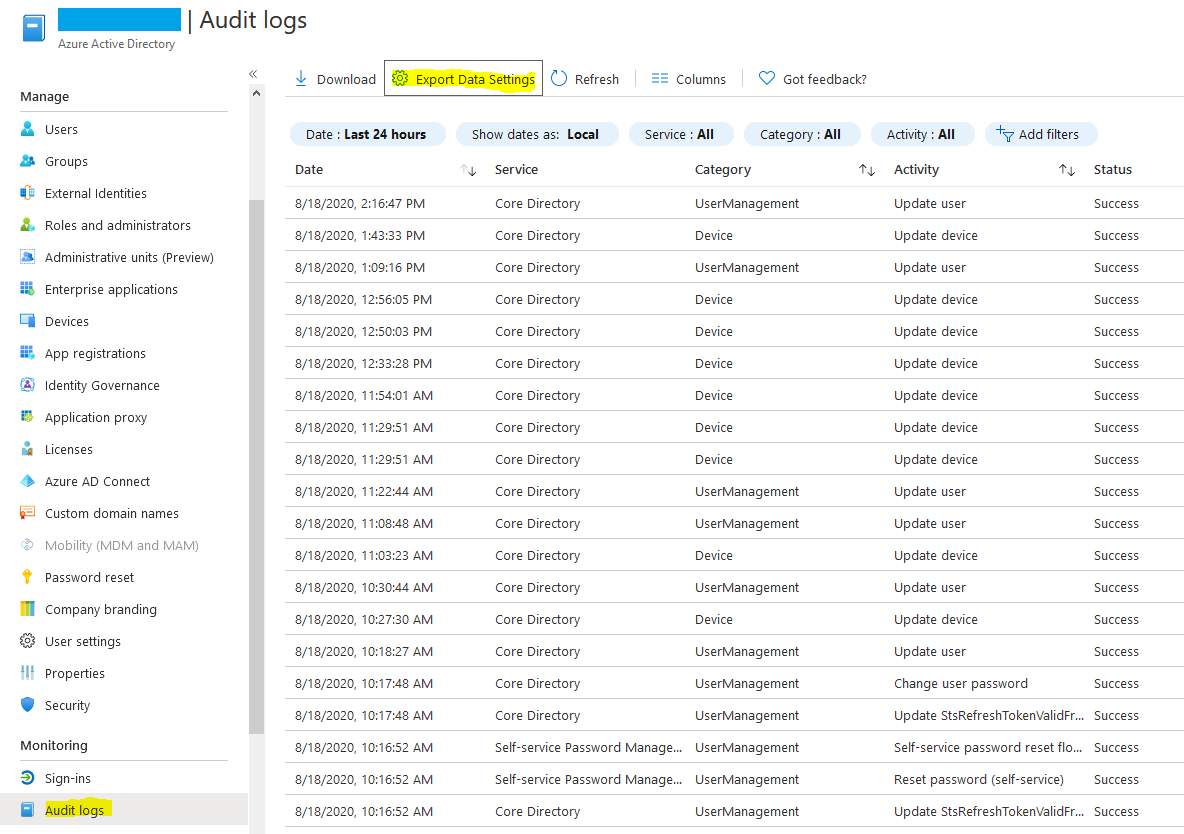
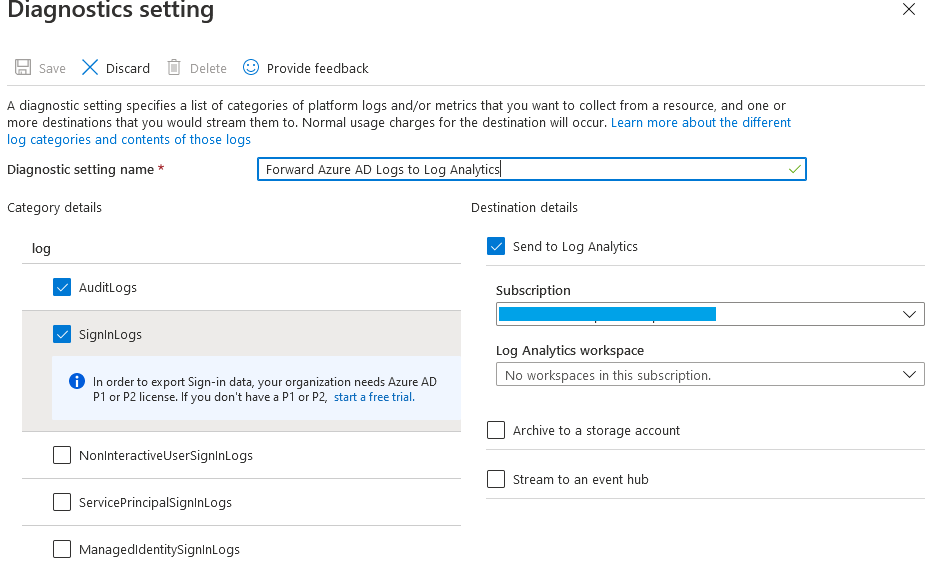
Setting up alerting on Conditional Access is quite straight forward and requires forwarding Azure AD logs to a Log Analytics Workspace. Forwarding these logs also has the added benefit of improving log retention past the default 30 days that is granted with an Azure AD Premium P1/P2 license.
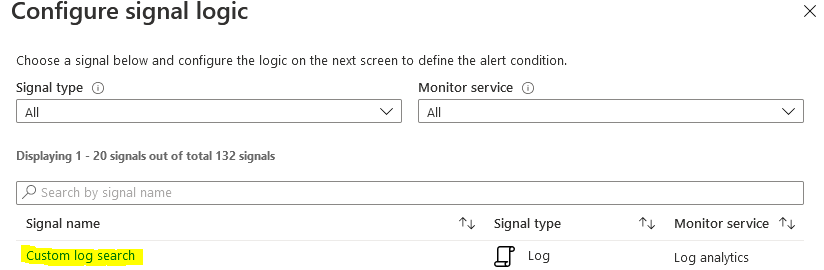
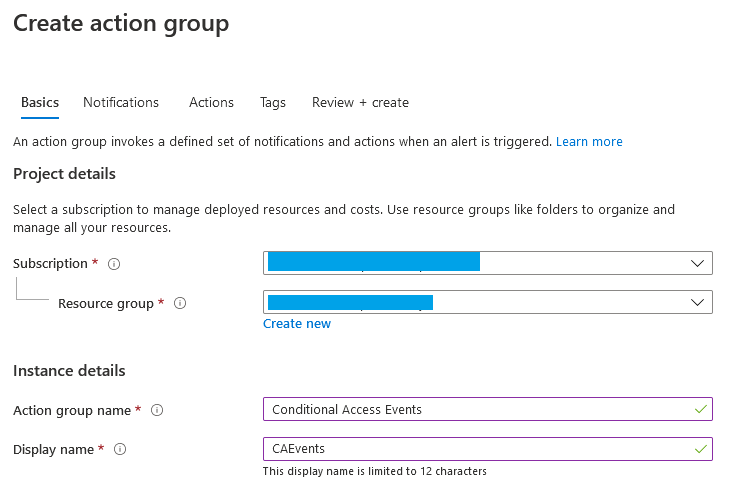
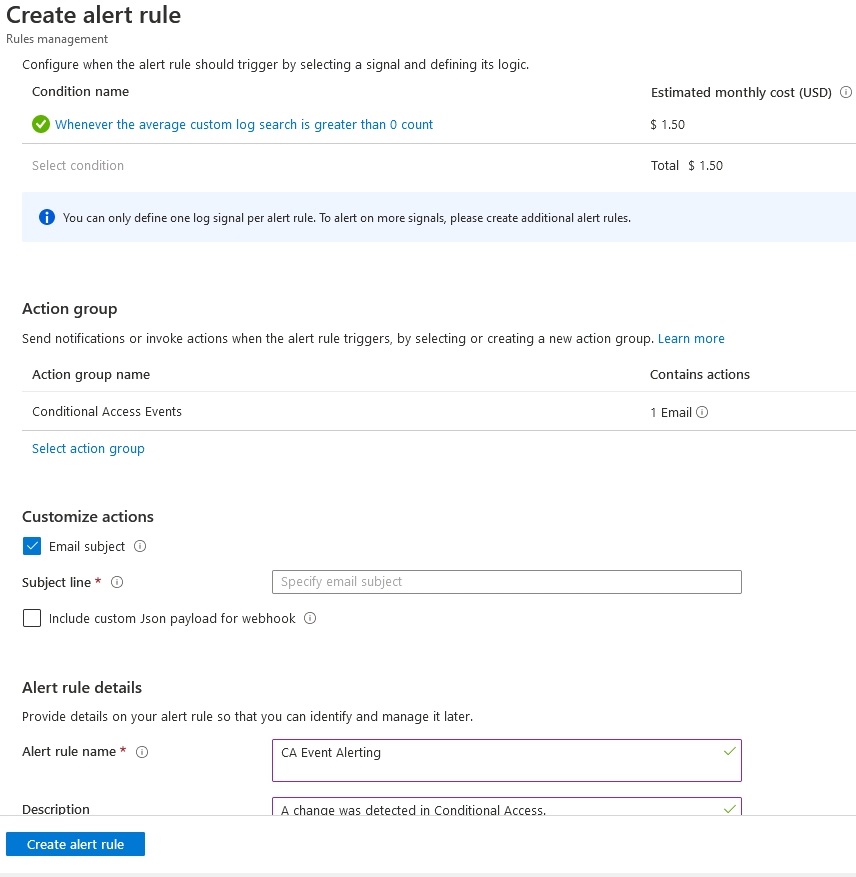
Today we will walk through setting up log forwarding and setting up two types of alerts. The first for catching changes to Conditional Access, and the second for catching changes to Conditional Access exempt groups.
kjhkjhkjhk