What is MFA?
For those that don’t know what MFA is, here’s the background info for context:
Passwords have proliferated across our online lives—they’re required for every single website and web application you use. As you know, this can be quite the headache—no one enjoys clicking the ‘forgotten password’ link and having to reset it for the umpteenth time. Historically, we used the same old trusty password for everything (and 59% of people still do). Then we realised how insecure passwords were and the more diligent of us moved to multiple passwords of higher complexity.
However, no matter how complicated your passwords are, there is always the threat of a brute force or spray attack cracking your password, a phishing email catching you out, or a data breach involving a company your details are registered with. Before you know it, your details could be for sale on the dark web. Want to see if your email addresses have ever been compromised? Check here at https://haveibeenpwned.com/ — it takes just a few seconds. You can also take this quiz from Google to see if you can spot a phishing email.
This is where MFA comes in. MFA allows you to add a second form of identity verification to your accounts in addition to your password—your password is the thing you know. The second form of identification must be something unique that you have (e.g. your phone or a FIDO2 security key) or something that you are (e.g. a biometric such as your fingerprint). These are common secondary verification factors. This means that even if your password details fall into the hands of an attacker, they can’t get in to your accounts without something unique to you like your mobile phone or fingerprint. These are not easy to get hold of for anyone, let alone a hacker who’s in Russia or China.
Typically, an average MFA system will generate a unique code each time you attempt to login—with the code being associated with your account. For example, you would enter your password and then you would be prompted to enter a code that will be sent to your phone via an SMS text or an email.
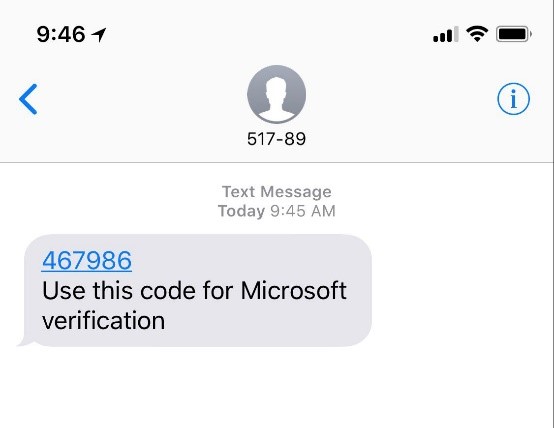
However, SMS MFA is not something your business should rely on. While it’s better than leaving MFA turned off, hackers can intercept SMS messages with relative ease—due to an ageing global phone-routing-system and the possibility of SIM Swap attacks.
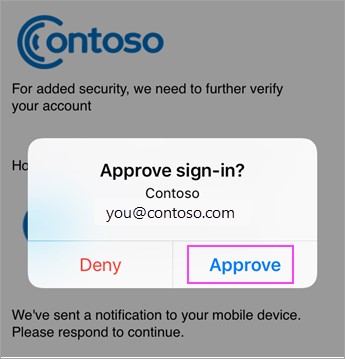
The latest and more secure version of MFA will send an approval notification to an authenticator app on your mobile device which allows you to simply click ‘approve’ or ‘deny’ to the request. You can quickly tap the prompt and you’ll be granted access.